-

Cybersecurity and Cloud Computing: 2015 Insights from Malcolm Shore
Malcolm Shore discusses the integration of cybersecurity practices with cloud computing technologies in these 2015 video presentations.
Read More » -

7 Ways to Ensure Cloud Computing Security
Here's a description for the article titled information security in cloud computing: Cloud computing offers scalable resources but introduces complex security challenges. This article explores key aspects of information security in cloud environments, discussing risks, best practices for data protection, encryption, access control, and compliance with standards like ISO/IEC 27017, to help organizations secure their cloud infrastructure effectively.
Read More » -

5 Essential Cloud Computing Security Tips
Security in cloud computing involves protecting data, applications, and infrastructure from threats, ensuring confidentiality, integrity, and availability. This article explores key security measures, best practices, and the challenges faced in securing cloud environments.
Read More » -

5 Essential Cloud Security Tips for Cloud Computing
The article titled cloud security cloud computing provides an in-depth look at the latest advancements and strategies in securing cloud computing environments. It explores various security measures, best practices, encryption techniques, compliance issues, and the evolving landscape of threats and protection mechanisms in cloud infrastructures. The piece is essential for IT professionals, business leaders, and anyone interested in understanding how to safeguard data and operations in cloud-based systems.
Read More » -
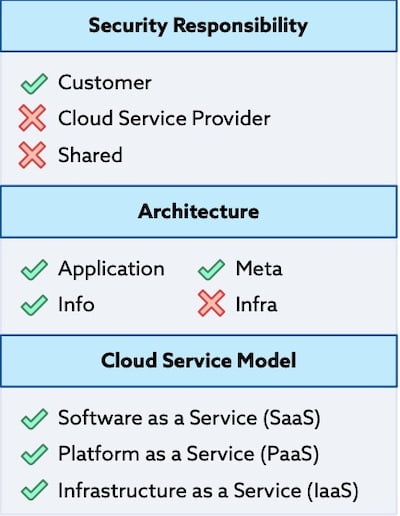
5 Essential Security Tips for Cloud Computing in 2023
Cloud computing security involves safeguarding data, applications, and infrastructure in a cloud environment through various strategies like encryption, identity and access management, and compliance with security standards to mitigate risks and protect against unauthorized access, data breaches, and other cyber threats.
Read More »