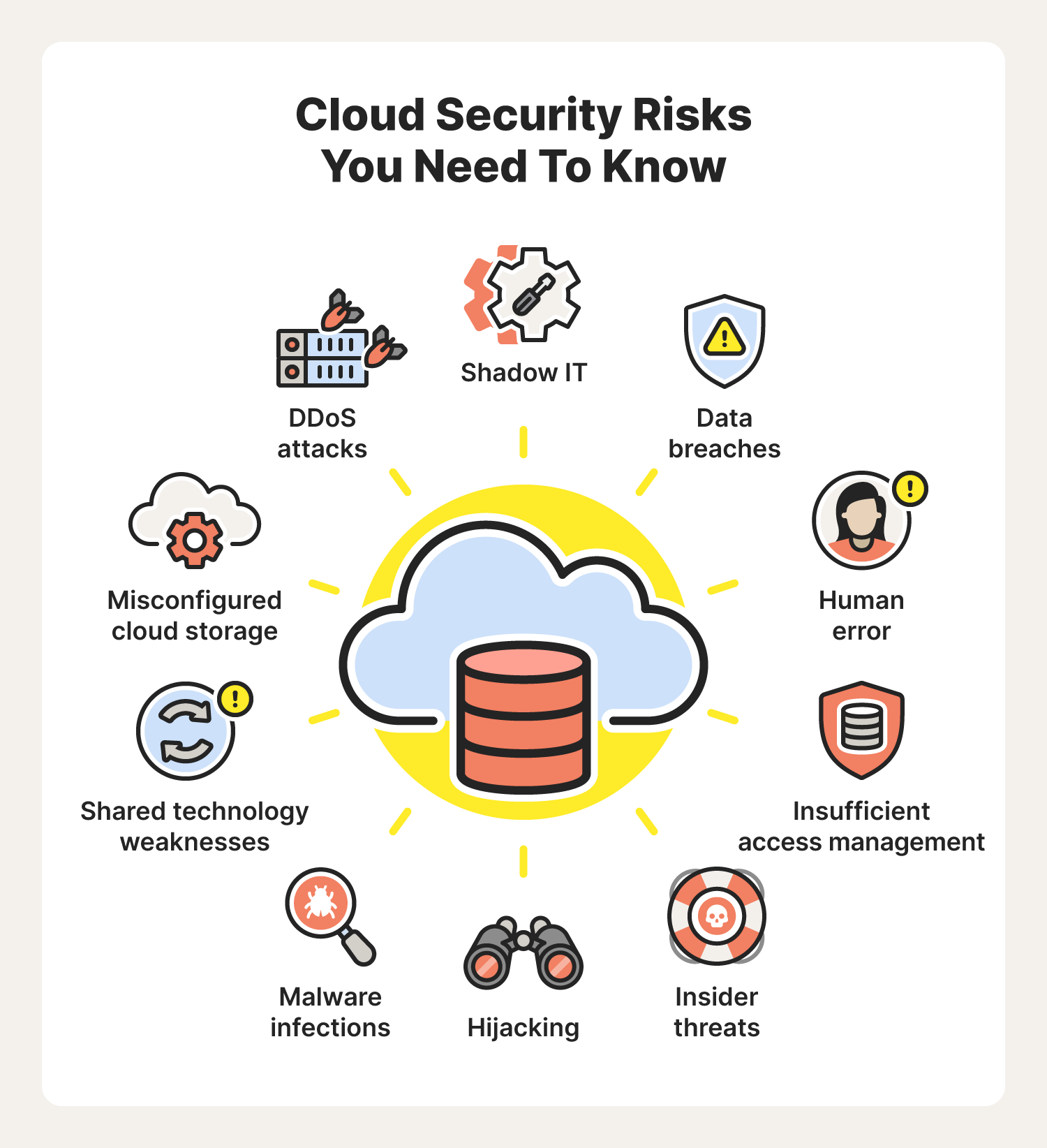
5 Essential Cloud Security Tips for Cloud Computing

In an era where businesses are increasingly transitioning to the cloud, understanding the nuances of cloud computing security has never been more critical. The cloud presents numerous advantages, including scalability, flexibility, and cost-effectiveness, but it also introduces a unique set of security challenges. Here's a comprehensive guide to help you enhance your cloud security measures effectively.
Understanding the Basics of Cloud Security
Cloud security isn’t just about keeping your data safe; it’s about safeguarding your company’s reputation, compliance with regulations, and overall operational integrity. Let’s delve into some of the fundamental aspects:
- Data Encryption: All data, especially during transit and at rest, should be encrypted to ensure confidentiality.
- Identity and Access Management (IAM): This controls who has access to what resources within your cloud environment.
- Network Security: Securing the network where your cloud services operate is vital, using firewalls, intrusion detection systems, and VPNs.
- Threat Detection and Monitoring: Continuous vigilance through logging and monitoring tools to detect any unusual or unauthorized activities.
Tip #1: Implement Multi-factor Authentication (MFA)
Multi-factor Authentication adds an extra layer of security by requiring more than one method of verification before granting access. Here’s how to implement MFA:
- Select a Robust MFA Solution: Choose an MFA service that supports various verification methods like SMS, push notifications, or hardware tokens.
- Configure MFA for Sensitive Services: Ensure MFA is enabled for all critical systems, particularly administrative access and APIs.
- Educate Users: Make sure your team understands why MFA is important and how to use it effectively.
🔐 Note: MFA can significantly reduce the risk of unauthorized access even if passwords are compromised.
Tip #2: Regularly Backup Your Data
Data loss can be catastrophic, but with regular backups, you can recover from disasters or cyberattacks. Here’s what you should consider:
- Set up automated backups at regular intervals.
- Verify the integrity and recoverability of your backups.
- Store backups in a different geographical location from your primary data center to ensure they are safe from regional incidents.
💡 Note: Test your recovery process regularly to ensure you can restore data when needed.
Tip #3: Segregate Your Network and Data
Segmentation limits the spread of breaches by isolating networks and data according to their sensitivity:
| Segmentation Level | Description |
|---|---|
| Network Segmentation | Divide the cloud network into zones or segments, each with its own security policies. |
| Data Classification | Classify data based on sensitivity (public, internal, confidential) and protect accordingly. |
Tip #4: Use Advanced Threat Detection Tools
Modern cloud environments are complex, and traditional security measures aren’t always enough. Advanced tools can:
- Monitor for unusual patterns or behavior in your cloud environment.
- Use machine learning to predict and prevent threats.
- Integrate with SIEM (Security Information and Event Management) for a centralized view of security activities.
Tip #5: Educate and Train Your Team
Human error remains one of the biggest security risks. Implementing a strong security culture includes:
- Regular training sessions on security best practices.
- Phishing simulations to test employee awareness.
- Creating a security-conscious atmosphere where every team member understands their role in maintaining security.
📚 Note: Security training should be an ongoing process, not a one-time event.
In conclusion, while the move to cloud computing brings a multitude of benefits, it necessitates a robust security framework to mitigate associated risks. Implementing these five tips – MFA, regular data backups, network and data segregation, advanced threat detection, and continuous employee education – forms the bedrock of a secure cloud environment. A proactive, layered approach to security can help you leverage the cloud's full potential while keeping your data and operations secure.
What is the difference between cloud security and traditional security?
+Cloud security focuses on protecting data, applications, and infrastructure that reside on cloud platforms, whereas traditional security typically refers to securing data centers, on-premise networks, and physical servers. Cloud security often involves shared responsibility models, encryption, and specific cloud-based security solutions.
How often should backups be made in a cloud environment?
+Backups in a cloud environment should be automated and can vary depending on the sensitivity of data. For critical systems, backups might be hourly or daily, while less critical data might be backed up weekly or monthly.
Is MFA enough to protect against cyber threats?
+MFA significantly enhances security by adding an extra layer of identity verification, reducing the chances of unauthorized access. However, it should be part of a comprehensive security strategy that includes other measures like encryption, access control, and monitoring.
Can cloud services be completely secure?
+No system is entirely secure, including cloud services. However, with the right practices, tools, and a shared responsibility model between cloud providers and customers, you can achieve a very high level of security.
Related Terms:
- cloud security best practices 2019
- best practices for cloud security
- how to improve cloud security
- cloud security concerns best practices
- how to manage cloud security
- cloud security monitoring best practices