Top 5 Cloud Computing Security Risks and How to Mitigate Them
In the rapidly evolving world of technology, cloud computing has emerged as a dominant force, enabling businesses to scale, innovate, and achieve greater flexibility. However, with the benefits come significant security risks that organizations must address to protect their data and operations. In this extensive guide, we'll delve into the top 5 cloud computing security risks and explore effective strategies to mitigate them, ensuring your cloud environment remains secure and trustworthy.
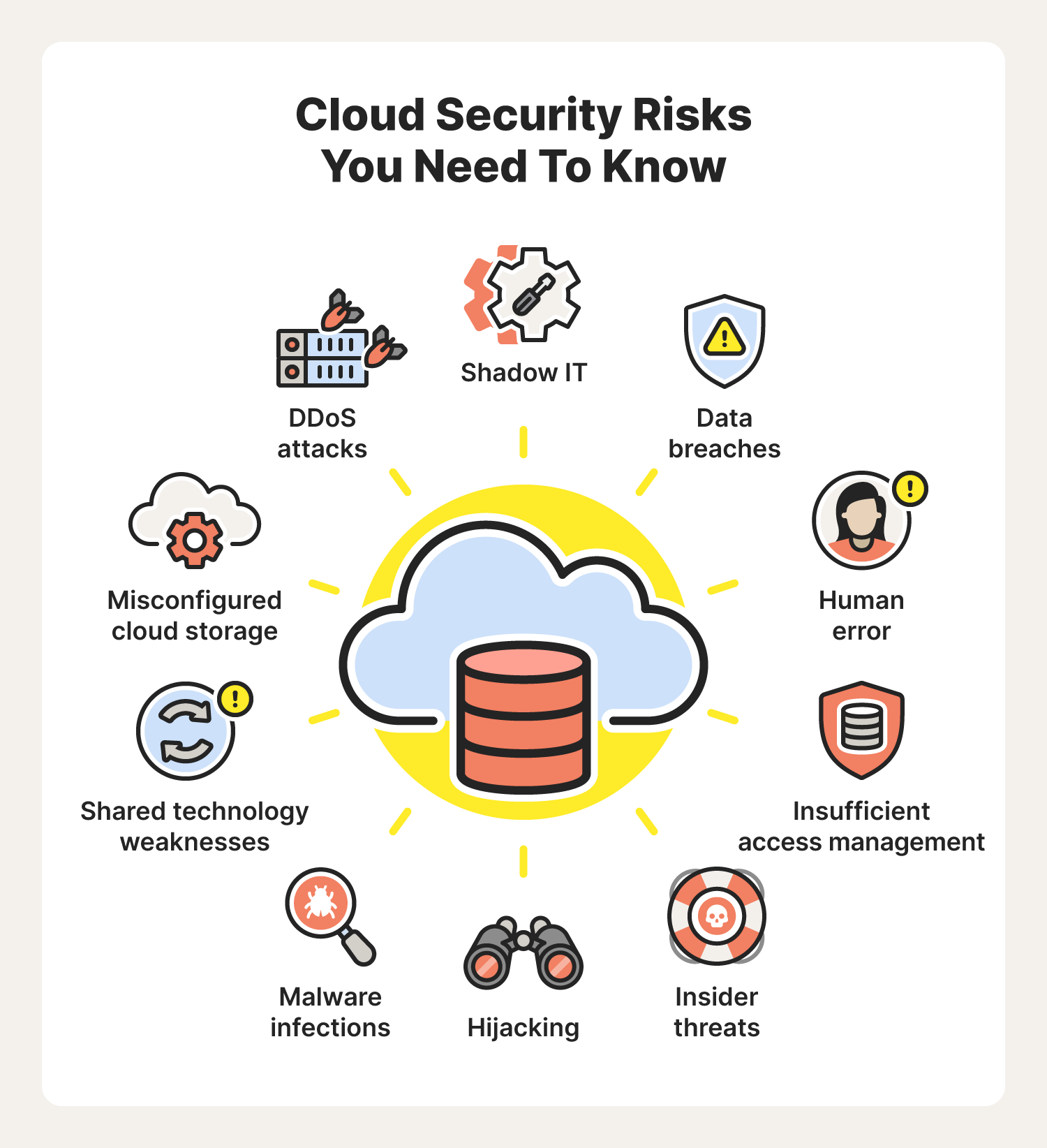
Data Breaches

A data breach in the cloud can be catastrophic, leading to loss of sensitive information, reputational damage, and financial loss. Here's how to mitigate this risk:
- Encryption: Use end-to-end encryption for data at rest and in transit. Secure cloud services often provide encryption as a default or an option.
- Access Controls: Implement rigorous access controls using principles like least privilege access, multi-factor authentication (MFA), and identity and access management (IAM) systems.
- Regular Audits: Conduct regular security audits to identify and rectify vulnerabilities. Automated tools can help in scanning for potential breach points.
- Data Masking: For non-production environments, data masking can help in protecting sensitive data during development or testing.
🔐 Note: Even with the best security practices, data breaches can happen. A robust incident response plan is crucial to minimize damage.
Insecure APIs

APIs are the glue of cloud services, but they can also be exploited if not properly secured:
- API Security Reviews: Regularly review API configurations and endpoints to ensure they are secure. This includes input validation, output encoding, and proper authentication.
- OAuth & OIDC: Use secure protocols like OAuth 2.0 and OpenID Connect (OIDC) for API access control.
- Rate Limiting: Implement rate limiting to prevent API abuse through excessive requests.
- Continuous Monitoring: Employ real-time monitoring solutions to detect unusual API behavior that might indicate an attack.
Insufficient Identity, Credential, and Access Management

Without proper management of identities, credentials, and access rights, unauthorized access to cloud resources can occur:
- Principle of Least Privilege: Ensure that users only have access to the resources necessary for their job functions.
- Strong Password Policies: Enforce complex passwords, regular password changes, and implement MFA wherever possible.
- Monitoring and Logging: Log and monitor access attempts, both successful and failed, to detect and respond to potential breaches.
- Regular Audits: Perform regular audits of permissions and remove any unnecessary access rights.
Account Hijacking

Account hijacking can lead to unauthorized access and misuse of cloud services:
- Multi-Factor Authentication (MFA): MFA is a must to ensure that even if passwords are compromised, additional verification is required.
- User Training: Educate users about phishing, social engineering, and the importance of maintaining account security.
- Anomaly Detection: Use AI-driven tools to detect unusual login attempts or access patterns.
- Session Management: Implement secure session management practices to prevent session fixation and hijacking.
🛡️ Note: Account hijacking can be mitigated by fostering a culture of security awareness. Train your users regularly.
Shared Technology Vulnerabilities

Many cloud services operate on shared infrastructure, which can lead to vulnerabilities if not managed correctly:
- Regular Security Patches: Keep all software, including operating systems and applications, up to date with the latest security patches.
- Virtual Machine Hardening: Ensure virtual machines are configured securely and unnecessary services are disabled.
- Segmentation: Use network segmentation to isolate sensitive data and services, reducing the attack surface.
- Vulnerability Management: Employ vulnerability management tools to identify and remediate potential weaknesses in your cloud environment.
Wrapping Up
In summary, cloud computing offers immense potential for businesses, but it requires vigilant security measures to mitigate its risks. By focusing on data protection, API security, access management, preventing account hijacking, and addressing shared technology vulnerabilities, organizations can enjoy the benefits of the cloud without compromising their security. This comprehensive approach to cloud security not only protects your data but also builds trust with clients and stakeholders, ensuring long-term sustainability and success in the digital age.
What is the primary risk associated with cloud computing?
+The primary risk associated with cloud computing is the potential for data breaches, where unauthorized users gain access to sensitive information.
How does encryption help in securing cloud data?
+Encryption converts data into a code to prevent unauthorized access. It ensures that even if data is intercepted or accessed, it remains unreadable without the proper decryption keys.
Why is multi-factor authentication crucial for cloud security?
+Multi-factor authentication adds an extra layer of security by requiring users to verify their identity through more than one method, making it much harder for attackers to gain access even if passwords are compromised.
Can shared infrastructure pose a security risk?
+Yes, shared infrastructure can lead to security risks if not properly managed, as vulnerabilities in the underlying technology can affect multiple users or tenants.
What should companies look for in a cloud service provider from a security standpoint?
+Companies should evaluate providers based on their security certifications, data encryption capabilities, compliance with industry standards, incident response capabilities, and the security measures for shared infrastructure.
Related Terms:
- Top cloud threats
- Top 5 cloud security threats
- Cloud computing risks and mitigation
- Cloud security challenges and solutions
- Top 10 cloud security risks
- Security disadvantages of cloud computing