5 Essential Tips for Secure Cloud Computing

Cloud computing has revolutionized the way businesses and individuals manage and process data, offering unparalleled scalability, flexibility, and cost-efficiency. However, with these benefits come security concerns that need to be addressed meticulously. In this article, we will explore five essential tips for secure cloud computing that can help protect your data and ensure safe online operations.
1. Understand Your Cloud Service Model
Before diving into cloud security, it’s crucial to understand the different service models available:
- Infrastructure as a Service (IaaS): This includes basic compute, storage, and networking resources where security measures are primarily managed by you.
- Platform as a Service (PaaS): Here, the provider manages the underlying infrastructure, but you are responsible for securing your applications and data on this platform.
- Software as a Service (SaaS): The provider handles most security aspects, including software updates, but you must ensure compliance and protect user data.
Each model has different security requirements, so knowing what your provider does versus what you need to do is foundational for securing your cloud environment.
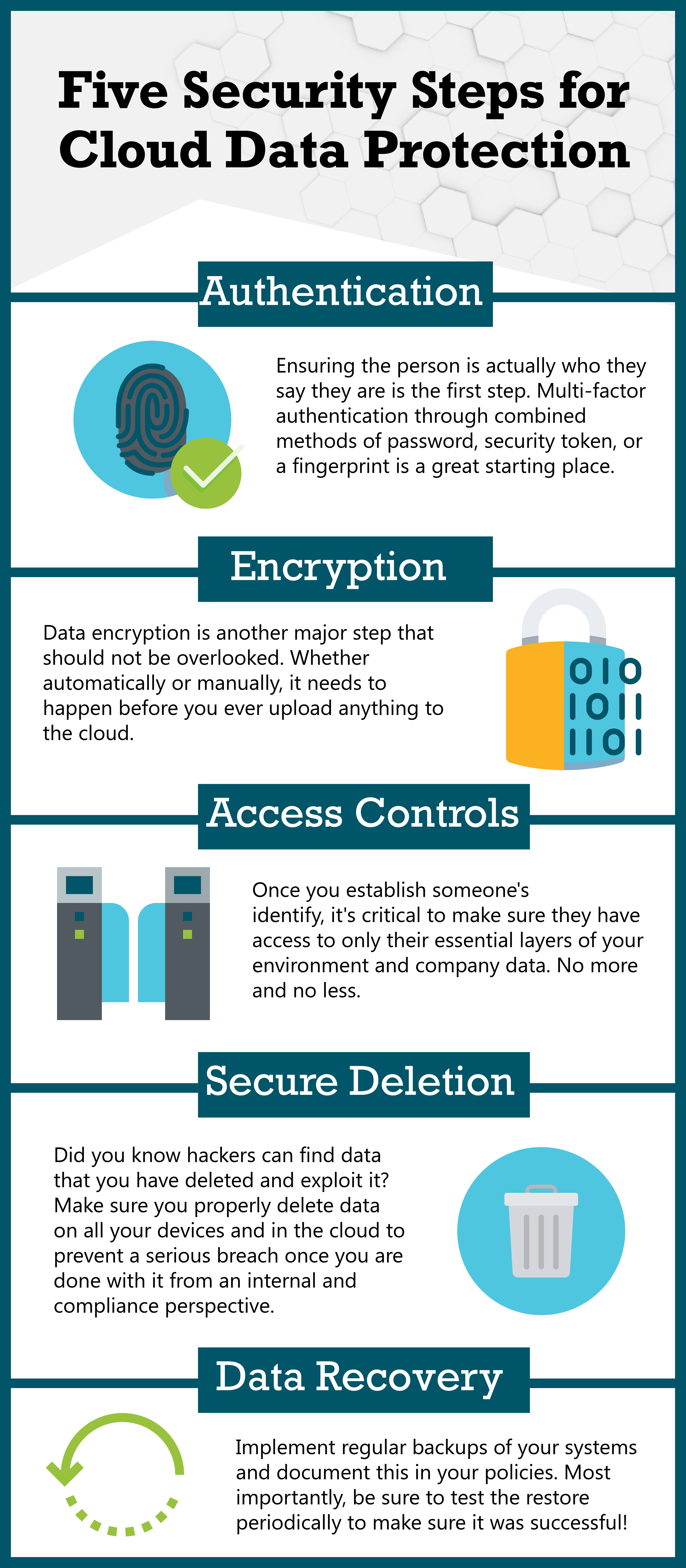
2. Implement Strong Identity and Access Management (IAM)
IAM is pivotal in cloud security because it controls who can access what in your cloud environment. Here are steps to secure IAM:
- Use Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring multiple forms of verification before granting access.
- Enforce Least Privilege: Users should only have the permissions they need to perform their job, reducing potential attack vectors.
- Regularly Audit Access: Review user permissions periodically to ensure they align with current roles.
- Implement Strong Password Policies: Require complex, regularly changed passwords to thwart brute-force attacks.
By focusing on these aspects, you can significantly reduce the risk of unauthorized access.
3. Data Encryption: From Transit to Rest
Encryption is your first line of defense against data breaches:
- Encryption in Transit: Secure Sockets Layer (SSL)/Transport Layer Security (TLS) protocols should be used to encrypt data as it moves between users and the cloud.
- Encryption at Rest: Data stored in the cloud must be encrypted, ensuring that even if someone gains access to your storage, they won’t understand the data without decryption keys.
- Key Management: Manage encryption keys effectively. You can either use key management services provided by your cloud provider or opt for a third-party solution.
These measures ensure that data remains confidential both while being transferred and while sitting idle.
4. Regular Security Assessments and Monitoring
Ongoing vigilance through assessments and monitoring is non-negotiable:
- Vulnerability Assessments: Regularly scan your cloud systems for vulnerabilities to proactively address security weaknesses.
- Penetration Testing: Simulate attacks on your cloud infrastructure to identify potential entry points for real-world attackers.
- Security Information and Event Management (SIEM): Implement SIEM tools to monitor logs for unusual activities, providing real-time alerts on potential breaches.
- Regular Audits: Perform audits to check compliance with internal security policies and regulatory requirements.
Monitoring and assessing the security posture of your cloud environment should be an ongoing process to keep security measures up to date with the evolving threat landscape.
5. Develop and Implement a Comprehensive Incident Response Plan
Even with the best security measures in place, breaches can still occur. Here’s how to prepare:
- Form an Incident Response Team: Have a dedicated team ready to respond to security incidents.
- Create an Incident Response Plan: Define clear steps for identifying, containing, eradicating, and recovering from security incidents.
- Run Drills: Conduct periodic drills to ensure your response plan is effective and that team members understand their roles.
- Post-Incident Review: After any security incident, review what happened, learn from it, and adjust your security protocols accordingly.
An effective incident response strategy can minimize damage, reduce recovery time, and often prevent future occurrences.
💡 Note: Always consider the shared responsibility model in cloud computing where security responsibilities are divided between you and your cloud provider. Understand this model well to ensure you're covering your part.
Security in the cloud is an ongoing commitment. By understanding your cloud service model, implementing robust IAM practices, encrypting data, continuously monitoring your systems, and being prepared with an incident response plan, you can safeguard your operations against potential threats. These five tips provide a roadmap to secure cloud computing, allowing you to leverage its benefits while protecting your most valuable assets.
What are the common cloud computing security threats?
+Common threats include data breaches, insecure APIs, compromised credentials, account hijacking, insider threats, and misconfigurations in cloud settings.
How does encryption work in the context of cloud computing?
+Encryption in cloud computing means converting readable data into a coded format that can only be accessed with decryption keys. It protects data both when it’s moving (in transit) and when it’s stored (at rest).
Why is IAM important in cloud security?
+IAM, or Identity and Access Management, ensures that the right individuals have the appropriate access to resources. It’s crucial for preventing unauthorized access, protecting against internal threats, and ensuring compliance with security policies.