Cloud Computing: Ensuring Your Network Security
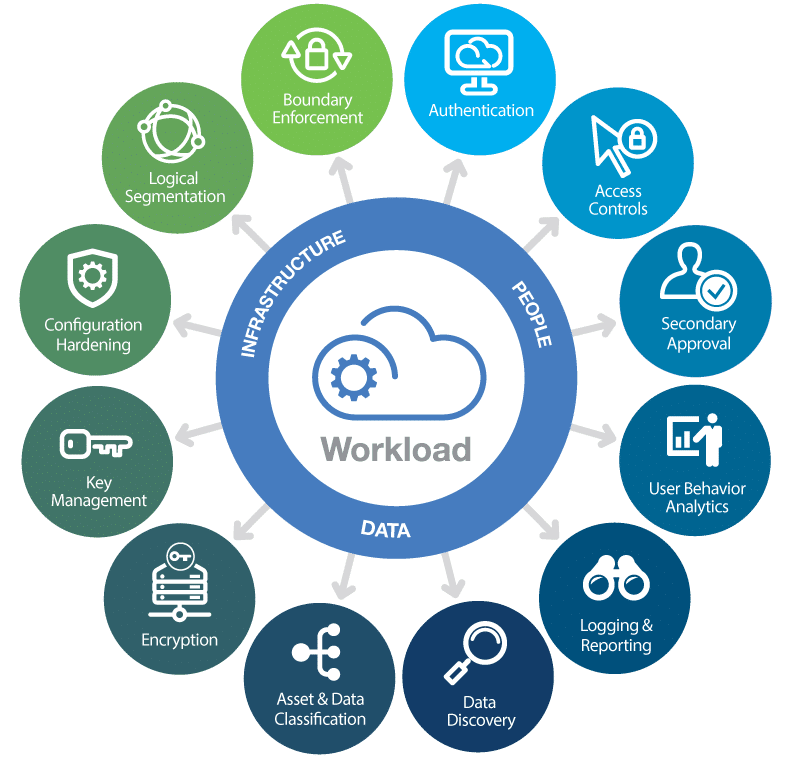
Understanding Network Security in the Cloud
The transition to cloud computing has revolutionized how organizations manage their IT infrastructure, offering scalability, flexibility, and cost-efficiency that traditional setups often can’t match. However, with these benefits come unique security challenges. Understanding and implementing robust network security measures is crucial to safeguard your data and systems when embracing cloud environments.
Cloud security encompasses various aspects, including protecting data both at rest and in transit, ensuring secure access to cloud services, and mitigating risks associated with shared technology environments. Here’s a comprehensive look at how you can enhance your network security in the cloud:
1. Data Encryption

Data encryption is the first line of defense against unauthorized access. Encrypting data before it reaches the cloud, often referred to as client-side encryption, ensures that even if your data were compromised, it would be nearly impossible to decipher without the encryption keys:
- Encryption at Rest: Use AES-256 encryption or similar strong algorithms to protect data when it’s stored in the cloud.
- Encryption in Transit: Implement TLS (Transport Layer Security) or IPSec (Internet Protocol Security) for securing data during transmission.
2. Identity and Access Management (IAM)

Identity and Access Management (IAM) controls who can access your cloud resources and what they can do with that access. Here are key strategies:
- Role-Based Access Control (RBAC): Implement fine-grained control over permissions by defining roles and associating them with users.
- Multi-Factor Authentication (MFA): Require users to provide multiple pieces of evidence to verify their identity.
- Single Sign-On (SSO): Streamline user access with a single set of credentials across different applications.
3. Network Security Configuration
Cloud providers offer several tools to help secure your virtual network infrastructure:
- Virtual Private Cloud (VPC): Isolate your cloud resources in a virtual network with a defined IP range.
- Security Groups and Network Access Control Lists (NACLs): Control inbound and outbound traffic at the instance and subnet level.
- Firewall: Use cloud-provided firewall services or third-party solutions to enforce security policies.
| Network Security Tools | Description |
|---|---|
| Security Groups | Virtual firewalls for Amazon EC2 instances, controlling both inbound and outbound traffic. |
| Network ACLs | An additional layer of security for controlling traffic at the subnet level, stateless by default. |
| Network Firewalls | Offer advanced features like deep packet inspection, intrusion detection, and prevention systems. |
🔐 Note: Always review and regularly update your security group rules and NACLs to match your evolving security needs.
4. Monitoring and Logging
Continuous monitoring and comprehensive logging are indispensable for a proactive approach to cloud security:
- Cloud Trail: Track user activity and API usage for AWS environments.
- Azure Monitor: For Microsoft Azure, offering insights into the health of resources.
- Google Cloud Monitoring: Provides visibility into resource usage and performance in Google Cloud.
Implementing centralized log management solutions can help in real-time threat detection, incident response, and compliance auditing.
5. Data Backup and Disaster Recovery
Despite the best security practices, unforeseen events can occur. Ensuring data backup and having a disaster recovery plan in place are critical:
- Regular Backups: Set up automated and regular backups, encrypting the backups to protect data integrity.
- Disaster Recovery: Develop and test a disaster recovery strategy to minimize downtime and data loss.
⚠️ Note: Regularly test your disaster recovery plan to ensure it's viable in a real-world scenario.
Summing Up
The journey to securing your network in the cloud involves understanding the shared responsibility model, where cloud providers secure the infrastructure, and you are responsible for securing your data, applications, and the management of access. Implementing the above measures—encryption, IAM, network configuration, monitoring, and data backup—helps build a comprehensive security strategy. Remember, cloud security is not a one-time setup but an ongoing process requiring vigilance, regular updates, and adherence to best practices to ensure your digital assets remain protected.
What is the primary responsibility of cloud providers in terms of security?
+
Cloud providers are responsible for the security of the cloud infrastructure, which includes securing the physical data centers, network infrastructure, and the hardware and software that form the cloud service itself.
How often should security policies be reviewed and updated?
+
Security policies should be reviewed and updated at least annually or after any significant changes to your cloud environment or new threats emerge.
Can encryption alone guarantee data security in the cloud?
+
Encryption is a crucial component, but it should be part of a broader security strategy that includes identity management, network security, monitoring, and regular audits.
Related Terms:
- Cloud network security best practices
- Cloud Network security course
- Cloud network security interview questions
- Google Cloud network security
- Cloud Network security certification
- cloud network security monitoring