Cloud Computing Network Security: Vital Tips for Safeguarding Your Data

The proliferation of cloud computing has transformed how businesses manage and protect their data. However, with this shift comes a unique set of security concerns. Securing data in cloud environments requires meticulous planning and implementation of specific strategies. Here, we delve into the critical steps that organizations can take to bolster their cloud computing network security and safeguard their valuable data.
Understanding Cloud Computing Security
Cloud computing involves delivering services such as storage, processing power, and applications over the internet. The onus of data protection shifts from the enterprise to the cloud service provider (CSP). However, despite outsourcing much of the infrastructure, your organization still needs to take proactive steps to secure your data:
- Shared Responsibility Model: Understand that while CSPs manage the security of the cloud, the security in the cloud is the responsibility of the customer.
- Multi-Tenancy: Cloud services often host multiple clients on the same hardware, making secure isolation crucial.
- Data Breach Risk: Cloud platforms can be high-value targets for cybercriminals seeking to access sensitive information.

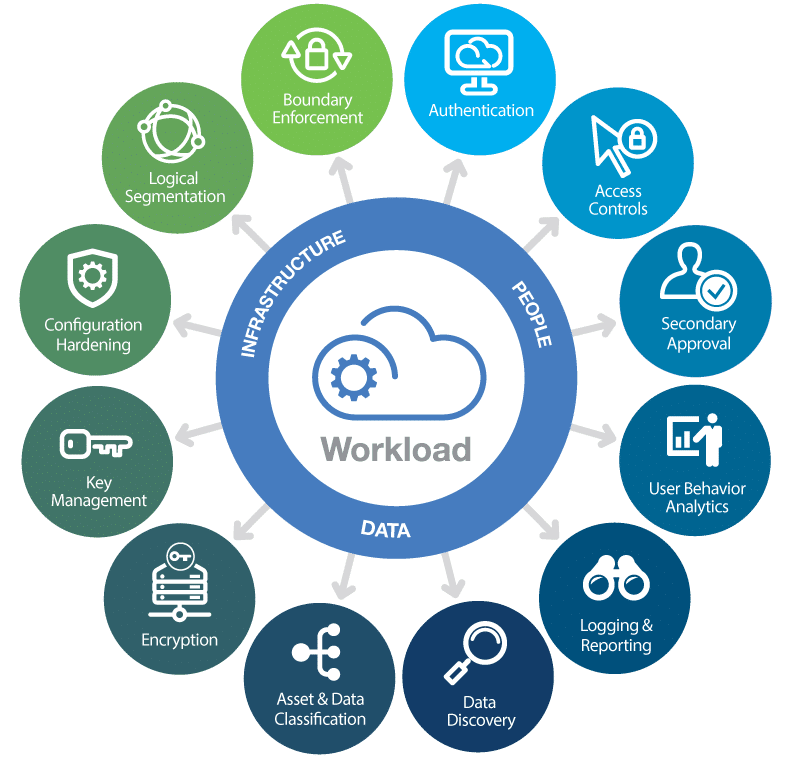
Essential Cloud Security Measures
Data Encryption
One of the first lines of defense in cloud security is encryption:
- Encryption at Rest: Ensure that your data is encrypted when stored in the cloud to prevent unauthorized access.
- Encryption in Transit: Use protocols like TLS (Transport Layer Security) to encrypt data moving between your organization and the cloud.
🔐 Note: Remember to regularly update your encryption protocols to guard against newly discovered vulnerabilities.
Identity and Access Management (IAM)
IAM is critical to control who can access what in your cloud environment:
- Role-Based Access Control (RBAC): Assign permissions based on roles rather than individual users to streamline management and reduce risk.
- Multi-Factor Authentication (MFA): Add an extra layer of security by requiring more than one form of authentication.
- Privileged Access Management (PAM): Manage administrative and high-level access to mitigate the risk of insider threats or unauthorized access.
Network Security Controls
Protecting the network infrastructure around cloud services is equally important:
- Firewalls and Intrusion Detection Systems: Deploy these to monitor and control incoming and outgoing network traffic.
- Virtual Private Cloud (VPC): Use VPCs to isolate your cloud resources from other tenants.
- Network Segmentation: Limit lateral movement within the cloud network by segmenting your network.
Security Monitoring and Logging
To maintain cloud security, ongoing monitoring and logging are essential:
- Continuous Monitoring: Implement real-time security monitoring to detect unusual behavior or breaches quickly.
- Log Management: Collect and analyze logs from all cloud services to track and respond to security events.
- Security Information and Event Management (SIEM): Use SIEM systems to correlate events and detect patterns that might indicate security incidents.
Advanced Security Techniques
Zero Trust Architecture
Implementing a Zero Trust model means:
- Verify Explicitly: Assume every connection is a threat and verify each request as if it originates from an open network.
- Least Privilege Access: Grant users the minimum access required to perform their jobs.
- Micro-Segmentation: Break down the network into small zones, each with its own security policies.
Cloud Security Posture Management (CSPM)
CSPM helps manage compliance and security across cloud environments:
- Automate compliance checks against predefined security standards.
- Identify misconfigurations in cloud setups before they become an issue.
- Provide visibility into the security state of the cloud infrastructure.

| Provider | CSPM Tool |
|---|---|
| AWS | Security Hub |
| Microsoft Azure | Azure Defender |
| Google Cloud | Security Command Center |
Incident Response in the Cloud
Be prepared to respond quickly to security incidents with:
- Incident Response Plan (IRP): Develop a comprehensive plan tailored to cloud-specific scenarios.
- Forensics Capabilities: Enable the collection of forensic data from cloud logs and virtual machines.
- Post-Incident Analysis: Conduct a thorough review post-incident to improve security measures.
Recapitulating the key points, safeguarding your data in a cloud computing environment involves a multi-layered approach. From understanding the shared responsibility model to implementing robust encryption and stringent access controls, every step is pivotal in defending against cyber threats. Effective security monitoring, adopting a Zero Trust model, and leveraging CSPM tools are vital to maintaining a secure cloud posture. Ensuring a swift and strategic incident response ensures that when breaches do occur, your organization can mitigate damage and recover promptly.
What are the common types of cloud security threats?
+Common cloud security threats include data breaches, insecure APIs, misconfiguration, account hijacking, insider threats, and DDoS attacks.
How often should security audits be performed in a cloud environment?
+Security audits should be performed at least quarterly, with continuous monitoring in between for real-time threat detection.
Is cloud computing inherently less secure than on-premises data centers?
+Cloud computing is not inherently less secure, but it requires a different security approach due to its distributed nature and the shared responsibility model.
Can a Zero Trust security model be applied to legacy systems?
+A Zero Trust model can be challenging to apply to legacy systems but can be retrofitted with careful planning and upgrades to system security capabilities.
What are the first steps to take when a cloud security incident occurs?
+Immediately contain the breach, isolate affected systems, begin forensic analysis, and notify stakeholders according to your incident response plan.
Related Terms:
- best data security in cloud
- data security in the cloud
- microsoft cloud data security
- cloud data security best practices
- data loss prevention in cloud
- data protection in cloud services