-

5 Essential Cloud Computing Security Tips for Businesses
Cloud computing security strategies, challenges, and best practices for protecting data in cloud environments.
Read More » -

7 Ways to Ensure Cloud Computing Security
Here's a description for the article titled information security in cloud computing: Cloud computing offers scalable resources but introduces complex security challenges. This article explores key aspects of information security in cloud environments, discussing risks, best practices for data protection, encryption, access control, and compliance with standards like ISO/IEC 27017, to help organizations secure their cloud infrastructure effectively.
Read More » -

7 Essential Tips for Cloud Computing Security
Here is a short description for the article titled cloud computing information security: Cloud computing presents unique security challenges; this article discusses strategies for safeguarding data and applications in a cloud environment, emphasizing encryption, access controls, and compliance with standards.
Read More » -

Cloud Computing Security Essentials: Safeguarding Your Data
Cloud computing offers scalability and efficiency but brings unique security challenges; this article examines essential security measures to protect data in cloud environments.
Read More » -
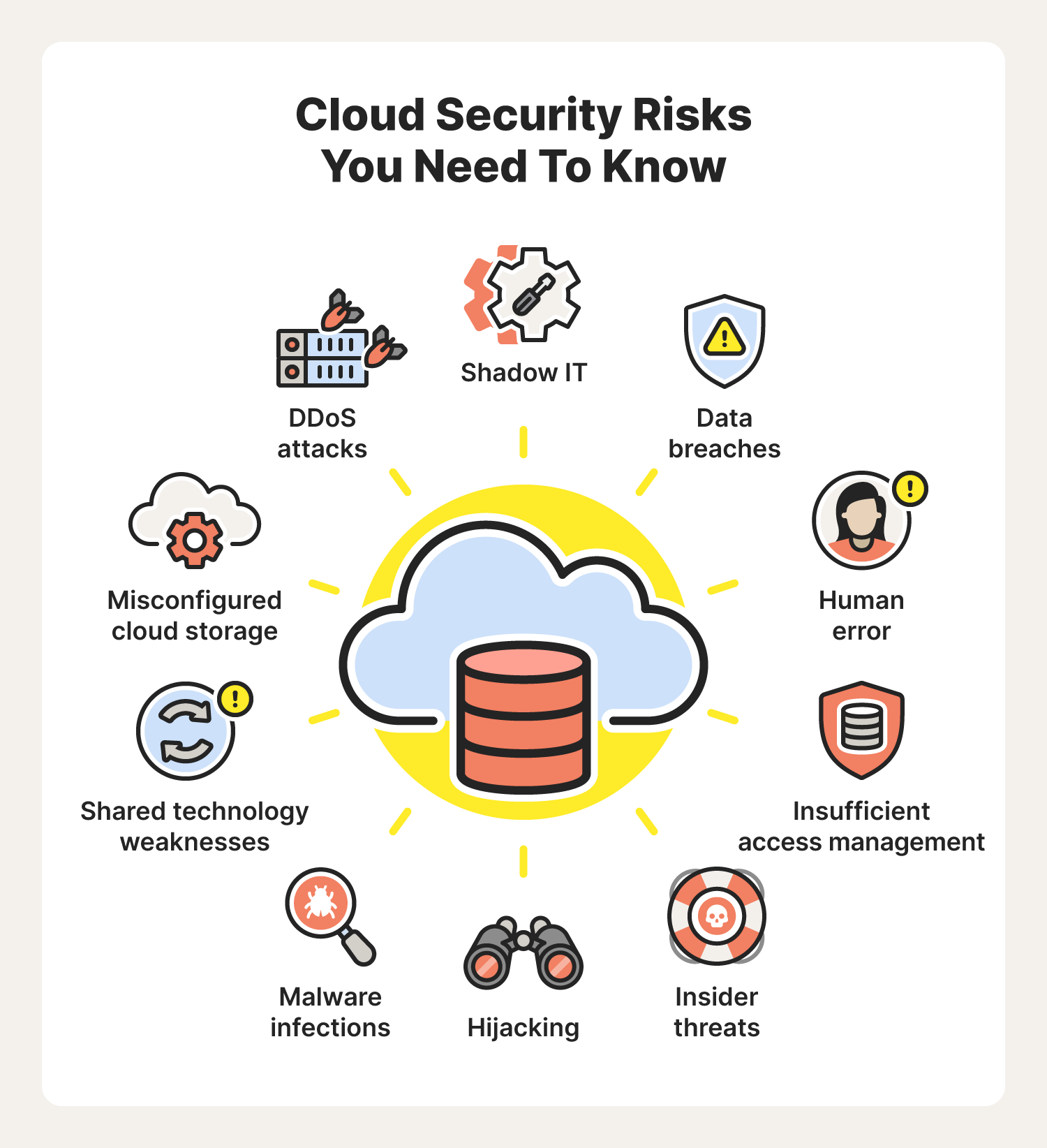
Top 5 Cloud Computing Security Risks and How to Mitigate Them
Cloud computing security encompasses various technologies, protocols, and best practices aimed at securing cloud-based infrastructure, platforms, and services. It addresses challenges like data protection, identity management, compliance, and privacy to ensure robust protection of assets in cloud environments. This article explores key security measures, risks, and strategies for safeguarding data in cloud computing.
Read More » -

Protecting Your Data in the Cloud: Essential Security Tips
Protecting sensitive information in cloud environments through encryption, access controls, and compliance with security standards.
Read More »