5 Essential Cloud Computing Security Tips for Businesses

In the digital age, where data breaches and cyber attacks are commonplace, securing sensitive business information becomes paramount. As more companies adopt cloud computing solutions for their scalability and efficiency, the importance of maintaining cloud security is more critical than ever. Here are five essential security tips to help businesses safeguard their data and operations in the cloud:
1. Implement Multi-Factor Authentication (MFA)

One of the most straightforward yet effective ways to enhance cloud security is through Multi-Factor Authentication (MFA). MFA adds an additional layer of protection by requiring users to confirm their identity through several verification methods, reducing the risk of unauthorized access even if passwords are compromised.
- Something you know: Traditional password or a passcode.
- Something you have: A physical device like a smartphone or security token.
- Something you are: Biometric factors like fingerprints or facial recognition.
By implementing MFA, businesses can significantly reduce the chances of an unauthorized entry, thereby enhancing their overall security posture.
2. Regularly Update and Patch Systems
Cloud environments are continuously updated by providers to fix bugs, enhance functionality, and most importantly, patch security vulnerabilities. Regular updates are crucial:
- To ensure all security patches are applied promptly.
- To keep systems up to date against the latest threats.
Businesses should:
- Automate updates whenever possible.
- Regularly review their systems to ensure all software is running the latest versions.
⚠️ Note: Ensure compatibility testing after updates to avoid disruptions.
3. Encrypt Data at Rest and in Transit
Encryption is the cornerstone of cloud security, protecting data from unauthorized access:
- At Rest: Encrypting data stored in cloud storage to prevent access by rogue insiders or hackers.
- In Transit: Securing data as it moves between the client and the cloud service provider through secure protocols like TLS/SSL.
By employing strong encryption standards, businesses ensure that even if data is intercepted or accessed, it remains unreadable without the correct decryption keys.
| Encryption Scenario | Method |
|---|---|
| Data at Rest | AES-256, PGP |
| Data in Transit | SSL/TLS |
4. Use Robust Identity and Access Management (IAM)
Identity and Access Management (IAM) ensures that only authorized personnel can access specific resources:
- Principle of Least Privilege: Grant only the necessary access rights to perform a job.
- Role-Based Access Control (RBAC): Assign permissions based on roles within the organization.
Proper IAM:
- Reduces internal risks and insider threats.
- Ensures compliance with data protection regulations.
💡 Note: Regularly audit access rights to maintain the principle of least privilege.
5. Conduct Regular Security Audits and Compliance Checks
Maintaining cloud security is an ongoing process. Here's what businesses should do:
- Regular Security Audits: Employ third-party audits or internal reviews to identify security gaps.
- Compliance Checks: Ensure adherence to industry standards like GDPR, HIPAA, or others applicable to your business.
By conducting regular audits:
- You can stay ahead of emerging threats.
- Identify and rectify any compliance issues before they become a problem.
In summary, as businesses increasingly rely on cloud computing for its numerous advantages, securing cloud environments becomes non-negotiable. By implementing Multi-Factor Authentication, keeping systems up to date, encrypting data, employing robust IAM practices, and conducting regular audits, companies can protect their cloud assets, maintain customer trust, and comply with regulatory requirements. These tips not only help in preventing security breaches but also foster a culture of security within the organization, making cloud computing not just efficient but also secure.
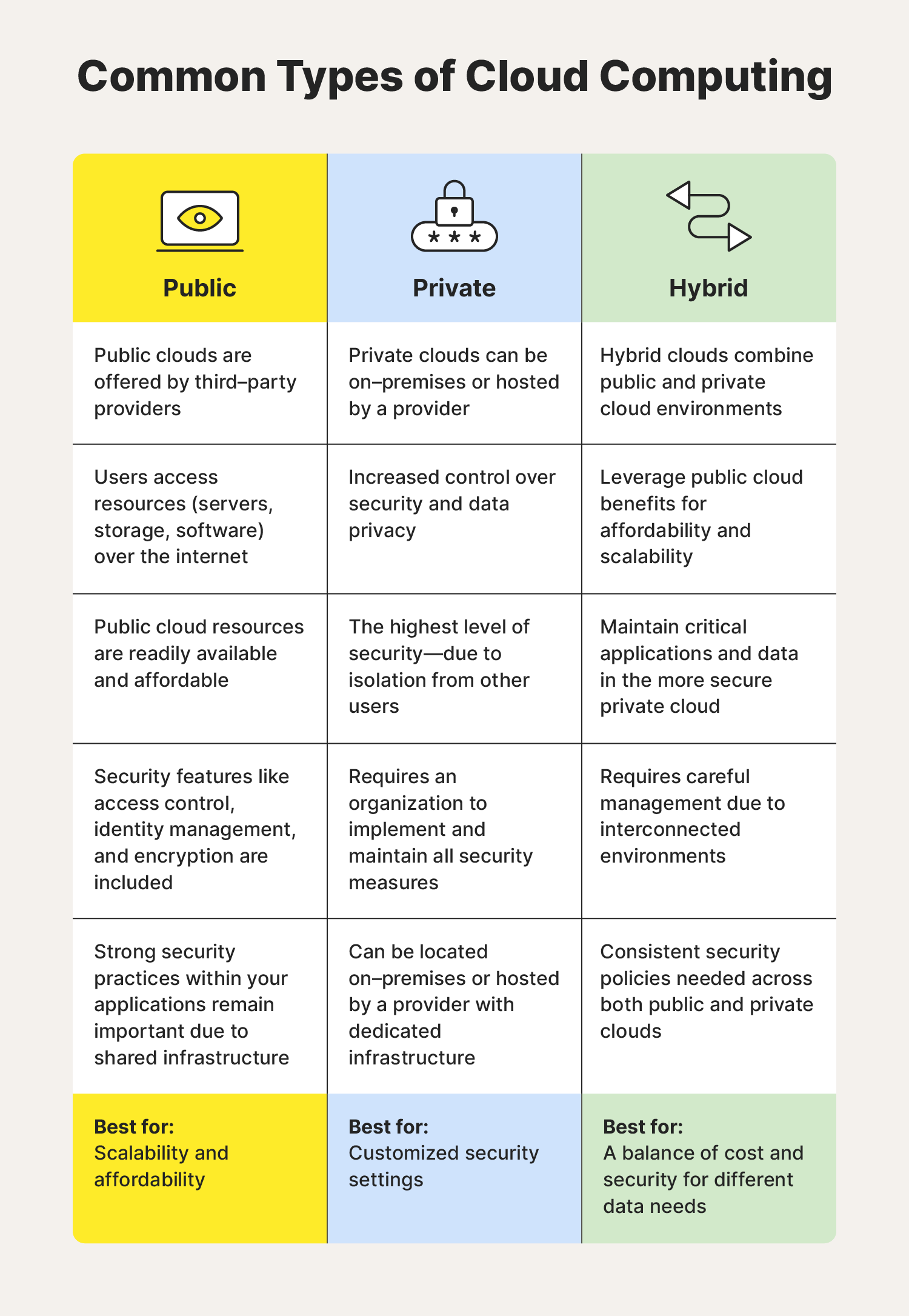
What is cloud computing?
+Cloud computing refers to the delivery of computing services—such as servers, storage, databases, networking, software, analytics, and intelligence—over the Internet (“the cloud”) to offer faster innovation, flexible resources, and economies of scale.
Why is cloud security important?
+Cloud security is crucial because businesses store sensitive data, including customer information, financial records, and proprietary data in the cloud. Breaches can lead to data theft, financial losses, damage to reputation, and regulatory penalties.
Can cloud computing be made as secure as on-premises infrastructure?
+Yes, with the right security measures in place, cloud computing can be as secure, if not more secure, than traditional on-premises solutions. The key is in implementing and maintaining robust security practices and using cloud services that comply with stringent security standards.
Related Terms:
- best practices for cloud computing



