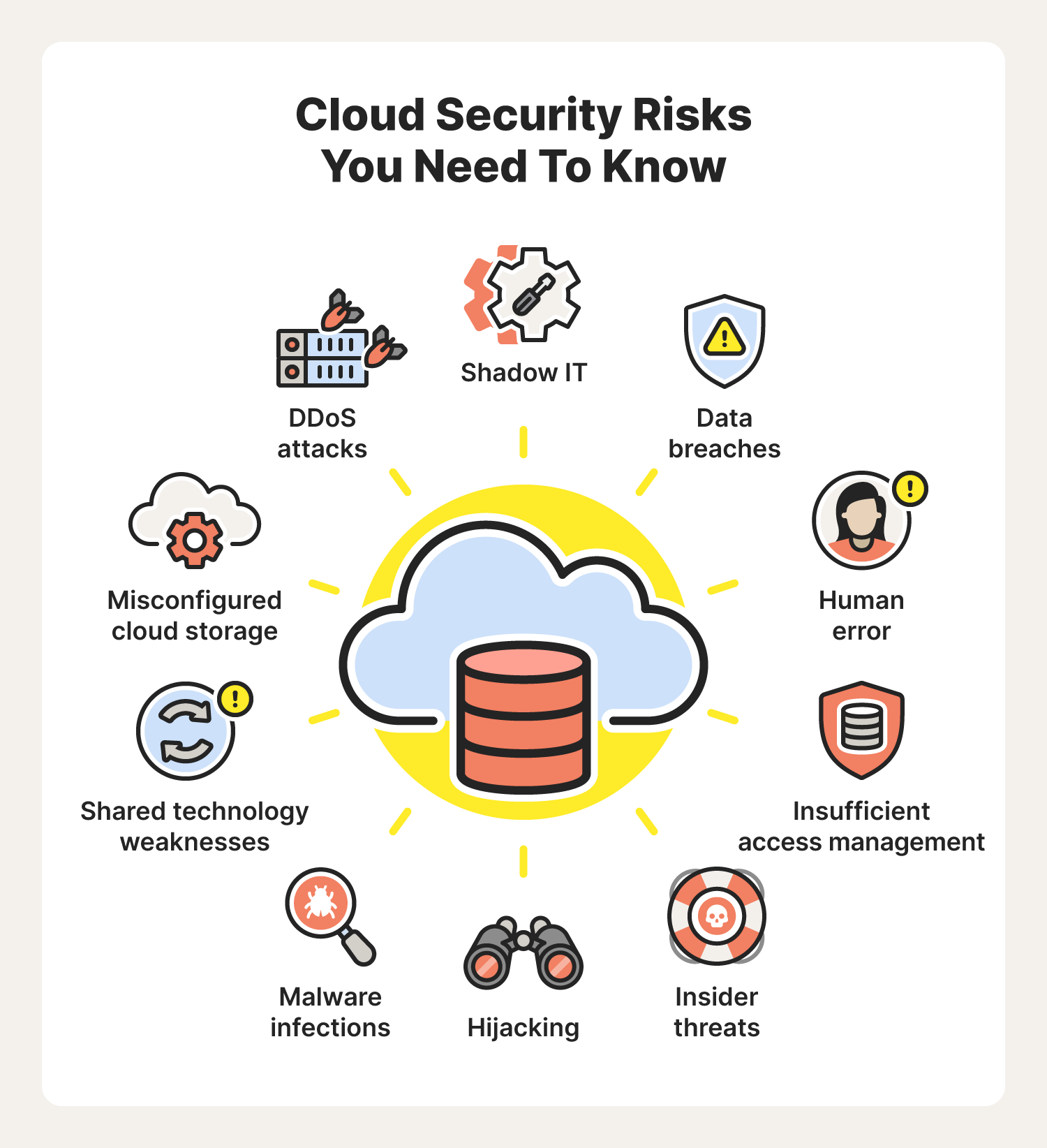
10 Cybersecurity Tips for Cloud Computing in 2015

In the modern digital landscape, cloud computing has become an indispensable component for businesses and individuals alike, offering flexibility, scalability, and significant cost savings. However, as reliance on cloud services grows, so does the importance of cybersecurity. Here are ten essential cybersecurity tips tailored for cloud computing environments in 2015, designed to keep your cloud infrastructure secure.
Assess Your Cloud Service Provider
Selecting the right cloud service provider is the first line of defense in your cloud security strategy. Here’s what to look for:
- Compliance with Security Standards: Ensure the provider adheres to standards like ISO 27001 or SSAE 16.
- Security Features Offered: Check for features like encryption, firewalls, identity and access management.
- Reputation and Past Security Incidents: Research their track record regarding security breaches or issues.
Implement Identity and Access Management (IAM)
Managing access to your cloud resources is crucial:
- Set up strict role-based access controls (RBAC).
- Use multi-factor authentication (MFA) for all user accounts.
- Regularly review and audit access permissions.
Use Encryption
Encryption is vital for protecting data both in transit and at rest:
- Ensure data is encrypted when it leaves your premises.
- Encrypt data at rest within the cloud storage.
- Implement end-to-end encryption for sensitive information.
Configure Network Security
Your network serves as the perimeter for cloud security:
- Utilize Virtual Private Clouds (VPCs) to isolate networks.
- Employ Network Address Translation (NAT) for enhanced security.
- Set up security groups and Network ACLs to control traffic flow.
Regular Vulnerability Assessments
Conduct routine vulnerability assessments:
- Perform internal and external scans to find weaknesses.
- Employ automated tools to simplify the process.
- Respond promptly to vulnerabilities with patches or workarounds.
Implement Security Automation
Automation can significantly boost your security:
- Automate updates for your software and security tools.
- Use automation for threat detection and incident response.
- Monitor for unauthorized access or unusual activity patterns.
Develop and Test Disaster Recovery Plans
Having a robust disaster recovery plan in place is critical:
- Define recovery time objectives (RTO) and recovery point objectives (RPO).
- Create and regularly test recovery procedures.
- Simulate data loss or cloud service outage scenarios to ensure recovery effectiveness.
Secure Your Endpoints
Endpoints like laptops, smartphones, and tablets can become entry points for attackers:
- Install and keep up-to-date anti-malware software.
- Configure mobile device management (MDM) to enforce security policies.
- Regularly audit endpoint security configurations.
Train Employees
Human error is often a significant factor in security breaches:
- Conduct regular training sessions on cloud security best practices.
- Teach employees to recognize and respond to phishing attempts.
- Ensure a culture of security awareness within the organization.
Legal and Compliance Considerations
Stay informed about legal and compliance requirements:
- Understand data residency laws to ensure compliance with where data is stored.
- Adhere to industry-specific regulations like HIPAA, GDPR, or PCI-DSS.
- Implement processes to meet audit and compliance requirements.
🌟 Note: Keeping your cloud infrastructure secure requires continuous vigilance and adaptation to evolving threats.
To wrap up, securing your cloud computing environment in 2015 involves a combination of choosing the right service provider, implementing strict access controls, employing encryption, maintaining network security, conducting regular assessments, automating security processes, planning for disaster recovery, securing endpoints, training employees, and considering legal and compliance issues. By adopting these tips, you fortify your digital resources against potential cyber threats, ensuring the safety and integrity of your data in the cloud.
What is the most critical aspect of cloud security?
+
The most critical aspect is securing data through encryption both in transit and at rest, along with rigorous access management.
Can I solely rely on my cloud provider for security?
+
While providers offer many security features, you should complement these with your own security measures tailored to your specific needs and risks.
What should I do if my data is compromised in the cloud?
+
Follow your disaster recovery plan to restore services, notify affected parties, and consider law enforcement involvement if necessary.
Related Terms:
- how to improve cloud security