5 Essential Tips for Cloud Computing Security

Cloud computing has revolutionized the way businesses manage and process their data, offering scalability, flexibility, and cost-efficiency. However, with these benefits come several security challenges. Here are five essential tips to ensure robust cloud computing security.
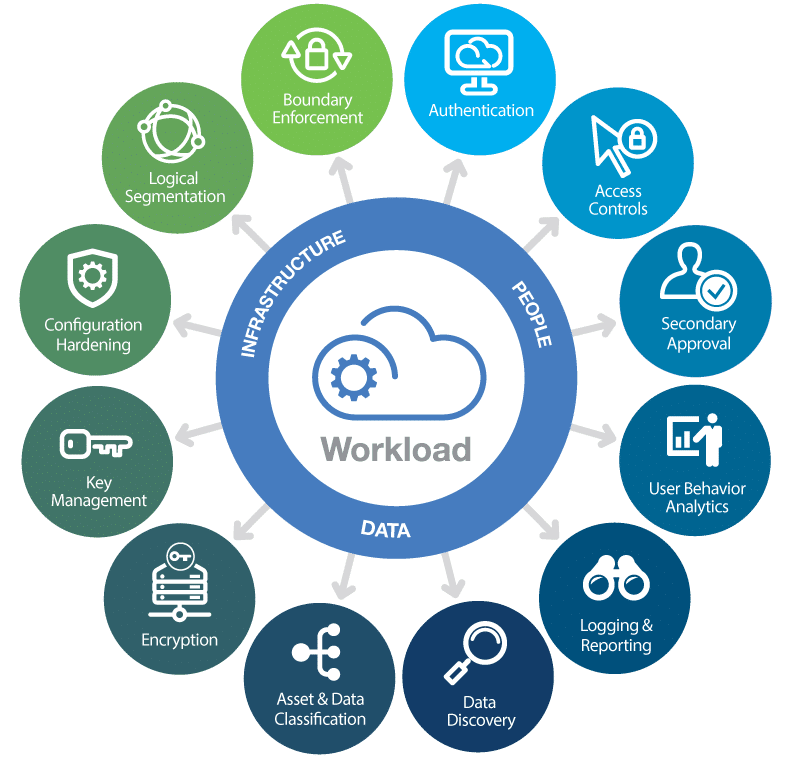
1. Strong Authentication and Access Control
Access control is the first line of defense in cloud security. Implementing strong authentication methods ensures that only authorized users can access cloud services:
- Multi-Factor Authentication (MFA): Use more than one authentication factor to verify identity. This could be something you know (like a password), something you have (like a mobile phone), or something you are (like biometrics).
- Role-Based Access Control (RBAC): Grant permissions based on the roles users perform within the organization to limit access rights to only what is necessary for their job functions.
- Regular Access Reviews: Regularly review and audit who has access to what. Revoke permissions that are no longer needed or have been compromised.
By enforcing strict access control measures, you significantly reduce the risk of unauthorized access.
2. Encrypt Data at Rest and in Transit
Encryption is vital for securing data, whether it's moving between the cloud provider's network or stored within:
- Encryption at Rest: Ensure data stored in the cloud is encrypted. This prevents unauthorized access to your data if storage is compromised.
- Encryption in Transit: Secure data as it moves to and from the cloud with protocols like TLS or SSL to prevent interception by malicious entities.
- Key Management: Manage encryption keys securely. Keep keys separate from the data they protect, and use services like Hardware Security Modules (HSMs) for key management.
Encryption safeguards your data against breaches and unauthorized viewing.
3. Implement Proper Backup and Disaster Recovery
Despite your best efforts, security incidents can occur. Here's how to prepare:
- Regular Backups: Back up your cloud data regularly to different environments or locations to ensure you can restore your data in case of a breach or data loss.
- Disaster Recovery Plan: Develop a comprehensive plan that outlines how to resume operations if a cloud service is compromised. This plan should include steps for data recovery, notification procedures, and continuity strategies.
- Data Replication: Replicate your data across multiple regions to reduce the risk associated with single-region outages or failures.
🚨 Note: Don't forget to test your disaster recovery plan regularly to ensure it works when you need it most.
4. Stay Ahead with Patch Management and Regular Updates
Cloud service providers release updates to fix known security vulnerabilities. Stay secure by:
- Timely Patching: Regularly apply patches and updates provided by cloud vendors to ensure your cloud infrastructure is protected against the latest threats.
- Automation Tools: Use automation tools to streamline the patch deployment process, reducing downtime and human error.
- Vulnerability Scanning: Conduct vulnerability scans after updates to ensure no new weaknesses are introduced with the patches.
This approach helps keep your cloud environment resilient against emerging threats.
5. Continuous Monitoring and Logging
To maintain cloud security, you need to have visibility into what's happening within your cloud environment:
- Real-Time Monitoring: Use tools to monitor for unusual behavior, unauthorized access attempts, and potential insider threats in real-time.
- Detailed Logging: Log all access and significant changes. Ensure these logs are stored securely and analyzed for anomalies.
- Alerting Mechanisms: Set up alerts to notify security personnel immediately when suspicious activity is detected.
With continuous monitoring, you can detect and respond to security incidents promptly.
Implementing these five tips for cloud computing security ensures a robust defense against potential threats. By combining strong access controls, encryption, comprehensive backup strategies, proactive patch management, and continuous monitoring, you create a secure environment that protects your cloud-based assets.
Incorporating these practices into your cloud security strategy not only enhances your security posture but also builds trust with your customers and partners by demonstrating a commitment to safeguarding their data in the cloud.
What is cloud computing security?
+
Cloud computing security refers to the set of practices, protocols, and controls used to protect data, applications, and infrastructure associated with cloud computing. It involves securing the infrastructure, applications, data, and various cloud deployment models from unauthorized access, alteration, or loss.
Why is encryption important in cloud security?
+
Encryption is crucial because it protects data both at rest and in transit from being accessed by unauthorized parties. Even if someone gains access to the cloud environment, encrypted data remains unreadable without the keys, providing an additional layer of security.
How often should cloud backups be performed?
+
The frequency of cloud backups depends on the criticality of the data. For highly critical data, daily or even real-time backups might be necessary. For less critical data, weekly or monthly backups might suffice. Regular testing of these backups is also recommended to ensure they can be restored when needed.
Related Terms:
- cloud security best practices 2019
- best practices for cloud security
- how to improve cloud security
- cloud security concerns best practices
- how to manage cloud security
- cloud security monitoring best practices