-

Cybersecurity and Cloud Computing: 2015 Insights from Malcolm Shore
Malcolm Shore discusses the integration of cybersecurity practices with cloud computing technologies in these 2015 video presentations.
Read More » -

5 Essential Tips for Secure Cloud Computing
This article discusses essential strategies and best practices for enhancing security in cloud computing environments.
Read More » -
Cloud Computing: Unlocking Data Security for Your Business
Cloud computing offers scalable resources, but data security remains a critical concern due to potential breaches and compliance issues.
Read More » -
5 Key Benefits of Hybrid Cloud Computing Solutions
Hybrid cloud computing solutions integrate both private and public cloud environments, offering businesses the flexibility, scalability, and cost-efficiency needed to optimize their IT infrastructure while ensuring data security and compliance.
Read More » -

Cloud Computing: Enhancing Security Measures for Better Protection
Cloud computing offers scalable, on-demand computing resources, but it also introduces unique security challenges that require robust strategies and continuous advancements to ensure data protection and compliance.
Read More » -

Secure Cloud Computing: Protecting Your Data Online
Secure cloud computing focuses on protecting data, applications, and infrastructure in cloud environments through encryption, identity and access management, and compliance with security standards to ensure data integrity, confidentiality, and availability.
Read More » -

7 Essential Tips for Cloud Computing Security
Here is a short description for the article titled cloud computing information security: Cloud computing presents unique security challenges; this article discusses strategies for safeguarding data and applications in a cloud environment, emphasizing encryption, access controls, and compliance with standards.
Read More » -
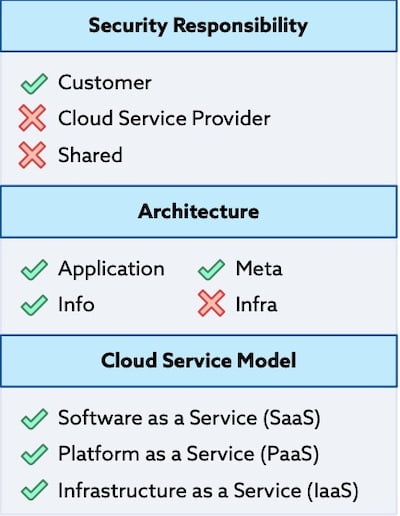
5 Essential Security Tips for Cloud Computing in 2023
Cloud computing security involves safeguarding data, applications, and infrastructure in a cloud environment through various strategies like encryption, identity and access management, and compliance with security standards to mitigate risks and protect against unauthorized access, data breaches, and other cyber threats.
Read More »
