Top 5 Security Solutions for Cloud Computing
In today's digital age, cloud computing has become a cornerstone of modern enterprise IT infrastructure. As organizations increasingly rely on cloud environments for data storage, processing, and application deployment, ensuring robust security measures has never been more critical. Here's a comprehensive look at the top five security solutions for cloud computing designed to protect your cloud-based assets from a myriad of threats.
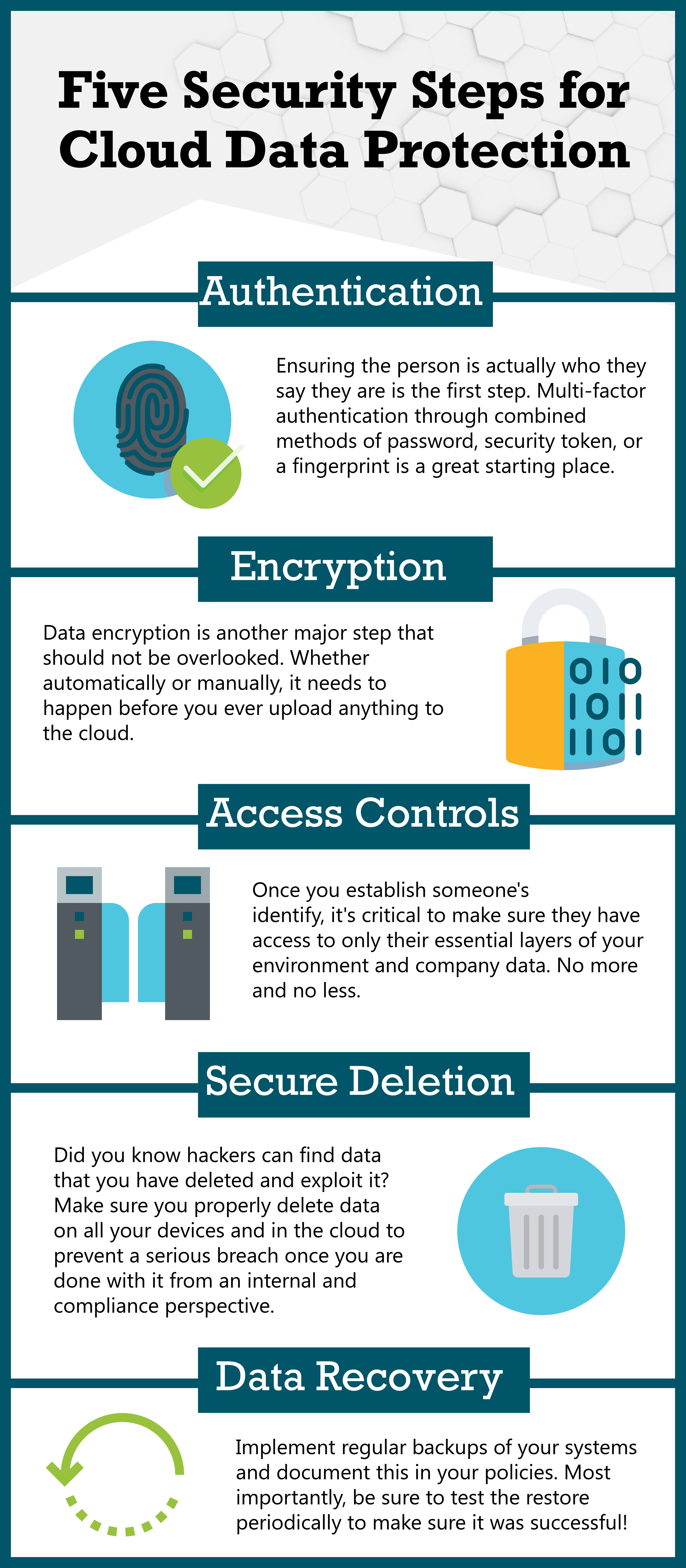
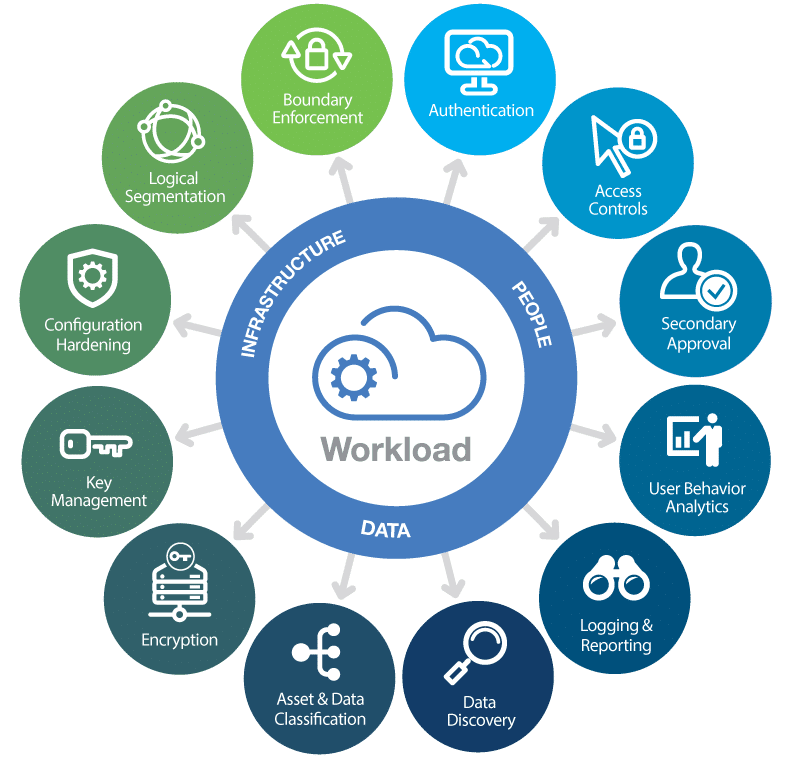
1. Identity and Access Management (IAM)

Identity and Access Management (IAM) serves as the first line of defense in any cloud security strategy. IAM solutions ensure that:
- Authentication is strengthened with multi-factor authentication (MFA), reducing the risk of unauthorized access.
- Authorization policies are enforced, granting users access only to what they need to perform their roles (principle of least privilege).
- Access can be monitored and audited for compliance and security investigations.
- Integration with identity providers (IdPs) for seamless single sign-on (SSO) across applications.
🔒 Note: Regularly review and audit your IAM policies to ensure they align with your security needs and comply with industry regulations.
2. Data Encryption

Data encryption is a vital security measure in cloud computing, ensuring that:
- Data is protected both at rest and in transit. This includes encryption in storage, during processing, and when being transmitted over networks.
- Key Management is handled securely, often involving Hardware Security Modules (HSMs) to manage encryption keys.
- Compliance with data protection regulations like GDPR, HIPAA, and others, which require encryption of personal data.
🔐 Note: Use a Bring Your Own Key (BYOK) approach to retain control over encryption keys even when using third-party cloud services.
3. Network Security

The cloud network layer must be fortified to prevent intrusions, data breaches, and other network-based attacks:
- Employ Virtual Private Clouds (VPCs) to isolate your cloud resources.
- Use firewalls, load balancers, and Web Application Firewalls (WAF) to filter traffic.
- Implement network segmentation for better traffic control and security.
- Utilize Secure Sockets Layer (SSL) / Transport Layer Security (TLS) for secure communication between nodes.
Here's a simple table outlining common network security tools:
| Tool | Description |
|---|---|
| Firewall | Monitors and controls incoming and outgoing network traffic. |
| VPC | Provides a virtual network for your cloud resources with configurable subnets. |
| Load Balancer | Distributes traffic to prevent network overload and DDoS attacks. |
4. Cloud Access Security Broker (CASB)

A CASB serves as an intermediary between cloud users and cloud services, providing visibility and control over cloud usage:
- Visibility into who is accessing your cloud environment, what they are doing, and the compliance status of these activities.
- Data Loss Prevention (DLP) by monitoring and controlling data flow to prevent unauthorized data transfers.
- Threat Protection through real-time anomaly detection and malware prevention.
- Compliance Monitoring to ensure cloud usage adheres to regulatory and organizational policies.
💼 Note: Always align your CASB implementation with your overall cloud security strategy to maximize effectiveness.
5. Security Information and Event Management (SIEM)

Security Information and Event Management (SIEM) tools aggregate log data from cloud applications, cloud services, and the underlying infrastructure to:
- Correlate events to detect security incidents in real time.
- Enable efficient incident response by providing a unified view of your cloud security landscape.
- Monitor and audit cloud usage for compliance with internal and external regulations.
- Generate actionable insights and reports for continuous improvement of security posture.
📊 Note: Regular tuning of your SIEM system is necessary to reduce false positives and improve detection accuracy.
Wrapping up, securing your cloud infrastructure is multifaceted, requiring a combination of IAM, encryption, network security, CASB, and SIEM solutions to provide comprehensive protection. By implementing these top five security solutions, organizations can confidently leverage the benefits of cloud computing while mitigating the associated risks. As cloud computing continues to evolve, so must our security strategies to ensure data integrity, privacy, and compliance in an ever-changing digital environment.
What is the difference between IAM and CASB?
+IAM focuses on managing access to resources based on user identities, whereas CASB provides additional visibility, control, and compliance enforcement over cloud service usage.
Can data be encrypted without affecting performance?
+Yes, modern encryption techniques, especially hardware-accelerated ones, can offer both security and high performance. However, some performance overhead can be expected, depending on the encryption method used.
How often should I update my cloud security policies?
+Security policies should be reviewed at least annually or following significant changes in your IT infrastructure, new regulatory requirements, or after security incidents.
Related Terms:
- Top 5 cloud security threats
- Security disadvantages of cloud computing
- Top 10 cloud security risks
- cloud security monitoring best practices
- cloud based cyber security solutions
- google cloud security solutions